Exploring the SHA-3/224 Generator: A New Standard for Secure Hashing
Created on 4 October, 2025 • Generator Tools • 34 views • 2 minutes read
The SHA-3/224 generator represents the future of cryptographic hashing — secure, efficient, and adaptable for modern needs.
In the evolving world of cybersecurity, hashing algorithms continue to play a vital role in protecting digital information. One of the latest advancements in this field is the SHA-3/224 generator, part of the SHA-3 (Secure Hash Algorithm 3) family. Designed to enhance both performance and security, SHA-3/224 offers a modern alternative to previous hashing standards like SHA-2, delivering improved resistance to advanced cryptographic attacks.
What Is a SHA-3/224 Generator?
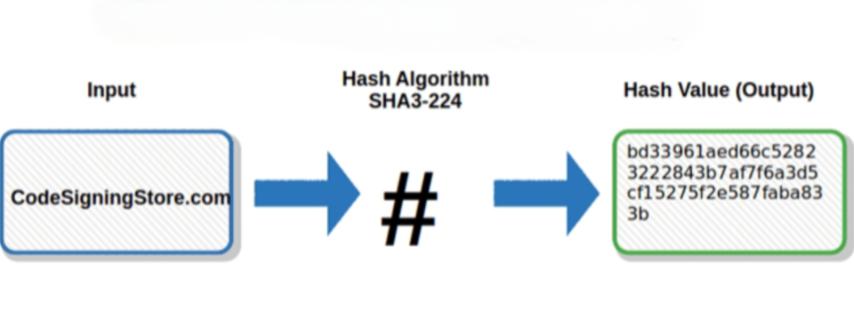
A SHA-3/224 generator is a cryptographic tool that produces a 224-bit (28-byte) fixed-length hash value from any input data, whether it’s a password, text, or file. Unlike its predecessors, which use the Merkle–Damgård construction, SHA-3/224 is built on the Keccak algorithm, a sponge-based construction that provides stronger resistance against collisions and preimage attacks.
When you input any piece of data into a SHA-3/224 generator, it processes that data through several rounds of transformations and outputs a unique hash value. Even a small change in the input (like adding a single space) results in an entirely different hash. This one-way, irreversible nature makes it ideal for security-sensitive applications such as password storage, digital signatures, and data integrity verification.
Why Use a SHA-3/224 Generator?
1. Next-Generation Security
The SHA-3 family was developed by the National Institute of Standards and Technology (NIST) as a successor to SHA-2. Unlike SHA-2, which could theoretically be vulnerable to certain future cryptographic attacks, SHA-3/224 uses a completely different internal structure. This gives it stronger protection against emerging threats such as length extension attacks.
2. Efficient and Flexible Performance
The SHA-3/224 generator is optimized for both hardware and software performance. It is efficient across various platforms, from embedded systems to large-scale servers. This flexibility allows developers to integrate SHA-3 hashing seamlessly into modern applications without heavy processing costs.
3. Compact Yet Powerful Output
The 224-bit output of SHA-3/224 makes it smaller and faster to process while still maintaining high cryptographic strength. This balance between size and security is particularly beneficial for systems that need to handle large volumes of data efficiently, such as authentication systems or blockchain applications.
4. Data Integrity and Authentication
A SHA-3/224 hash ensures that data remains unchanged during transmission or storage. If even a single bit of the original data is altered, the hash result will completely change. This makes it a reliable method for verifying file integrity, validating software updates, and securing communications.
How to Use a SHA-3/224 Generator
Using a SHA-3/224 generator is straightforward and accessible to anyone:
- Input your data or text — this could be a password, message, or file.
- Run the hash function — the generator applies the SHA-3/224 algorithm to your input.
- Receive the 224-bit hash output — a unique, irreversible digital fingerprint.
Many online tools and programming libraries (like Python’s hashlib) support SHA-3/224, making it easy to integrate into both personal and professional security systems.
Conclusion
The SHA-3/224 generator represents the future of cryptographic hashing — secure, efficient, and adaptable for modern needs. With its sponge-based Keccak design, it offers superior protection against evolving threats while maintaining excellent performance across platforms. Whether you’re securing passwords, verifying files, or building blockchain solutions, SHA-3/224 ensures your data remains safe, trustworthy, and future-proof.