Exploring the Role of a SHA-384 Generator in Modern Data Security
Created on 3 October, 2025 • Generator Tools • 63 views • 2 minutes read
A SHA-384 generator is more than just a tool—it is a cornerstone of modern cybersecurity practices.
Introduction to SHA-384 Generator
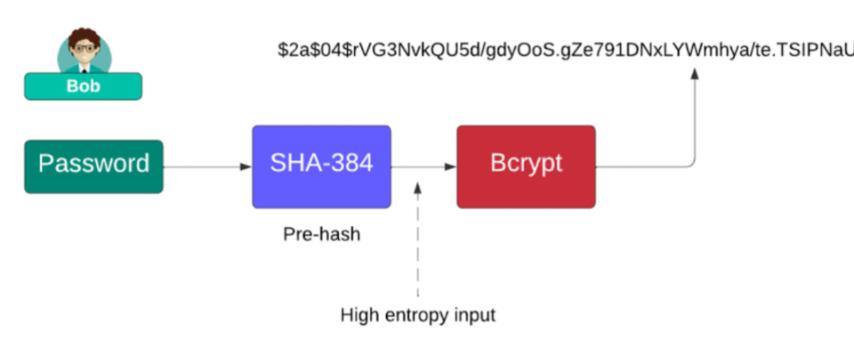
When it comes to cryptographic hashing, security professionals rely on advanced algorithms to protect sensitive information. Among these, the SHA-384 generator plays a crucial role in ensuring data integrity and authentication. SHA-384 is a member of the SHA-2 family of hashing algorithms, designed by the National Security Agency (NSA) and standardized by NIST. It produces a 384-bit hash value that is more secure than SHA-256 but lighter than SHA-512, making it an excellent balance between performance and protection.
With its wide applications in digital signatures, password storage, and secure communication, SHA-384 is highly valued in industries that demand robust security measures.
What is a SHA-384 Generator?
A SHA-384 generator is a tool that transforms any input—whether text, files, or binary data—into a fixed-length hash output consisting of 96 hexadecimal characters. This output, known as a hash, is unique to the input and serves as a digital fingerprint.
Key Features of SHA-384:
- Irreversible: The generated hash cannot be converted back to the original input.
- Collision Resistant: It is designed to minimize the chances of two different inputs producing the same hash.
- Consistency: Regardless of input size, the hash output always has the same fixed length.
Why Use a SHA-384 Generator?
1. Data Integrity
By comparing hash values, you can confirm that information has not been altered during transmission or storage.
2. Secure Authentication
Many systems use SHA-384 to hash passwords and authentication keys, ensuring that sensitive data remains hidden from attackers.
3. Digital Signatures
SHA-384 is frequently used in SSL/TLS certificates and secure communication protocols, adding trust and authenticity to digital exchanges.
4. Compliance and Security Standards
Organizations dealing with financial data, healthcare information, or government records often use SHA-384 to comply with strict cybersecurity standards.
How to Use a SHA-384 Generator
Using an online or software-based SHA-384 generator is simple:
- Enter the desired text, file, or data into the generator tool.
- Click the "Generate" or "Hash" button.
- The tool will instantly create a 96-character hexadecimal string as the SHA-384 hash.
For example:
- Input: hello world
- Output (SHA-384): fdbd8e... (truncated for readability)
This hash output will remain consistent for the same input, making it useful for verification purposes.
Advantages of SHA-384 Over Other Hash Algorithms
Compared to older algorithms like MD5 or SHA-1, SHA-384 provides significantly stronger security. It reduces vulnerabilities to brute-force and collision attacks, making it a preferred choice for industries that demand higher levels of encryption without the heavier computation load of SHA-512.
Conclusion
A SHA-384 generator is more than just a tool—it is a cornerstone of modern cybersecurity practices. From securing passwords and validating digital signatures to safeguarding sensitive transactions, SHA-384 offers a strong balance of performance and reliability. For developers, IT professionals, and organizations alike, adopting SHA-384 ensures greater confidence in protecting digital assets against emerging threats.