Unlocking the Power of a SHA-256 Generator: Secure Hashing Explained
Created on 3 October, 2025 • Generator Tools • 30 views • 2 minutes read
A SHA-256 generator is more than just a hashing tool—it is a foundation of secure digital communication, password protection, and blockchain technology.
Introduction to SHA-256 Generator
In today’s digital era, data security has become one of the most critical aspects of online interactions. One of the most reliable methods to safeguard information is through hashing, and the SHA-256 generator stands as a trusted tool in this area. SHA-256 (Secure Hash Algorithm 256-bit) is a member of the SHA-2 family developed by the National Security Agency (NSA). It produces a fixed 256-bit hash value, ensuring that sensitive information remains protected, unalterable, and verifiable.
Whether you’re a developer, a security professional, or simply someone who wants to understand how data integrity is preserved, knowing how an SHA-256 generator works is essential.
What is a SHA-256 Generator?
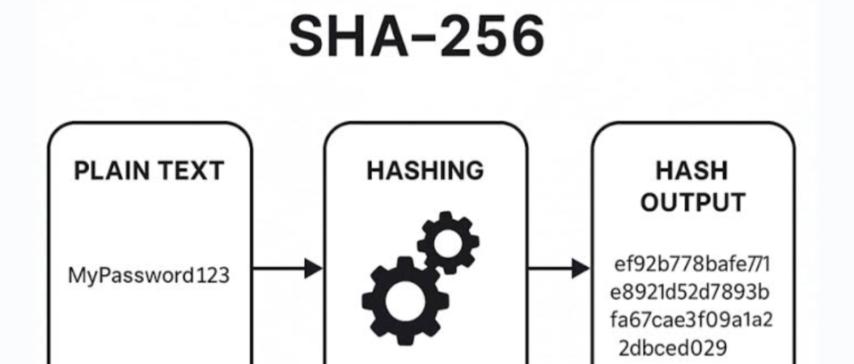
A SHA-256 generator is a digital tool that converts any input—such as text, file data, or passwords—into a 64-character long string of alphanumeric characters. This unique output is known as a hash.
The key features of SHA-256 include:
- Irreversibility: Once data is hashed, it cannot be reversed to reveal the original input.
- Uniqueness: Even a tiny change in the input leads to a completely different hash output.
- Consistency: The output is always 64 characters regardless of the input size.
This makes SHA-256 highly useful in various applications, from password storage to digital signatures and blockchain technology.
Why Use a SHA-256 Generator?
1. Data Integrity
SHA-256 helps verify that data hasn’t been tampered with during transmission. By comparing hash values, you can confirm authenticity.
2. Password Security
Many systems store passwords in their hashed form using SHA-256, ensuring that even if a database is leaked, actual passwords remain hidden.
3. Blockchain Applications
Cryptocurrencies like Bitcoin rely heavily on SHA-256 to secure transactions and maintain the blockchain’s integrity.
4. Digital Signatures
A SHA-256 generator allows developers to create secure digital signatures, ensuring trust in online communication and agreements.
How to Use a SHA-256 Generator
Using an SHA-256 generator is straightforward:
- Enter the text, file, or data you want to hash.
- Click the "Generate Hash" button.
- The tool will instantly produce a unique 64-character hash string.
For example:
- Input: hello
- Output (SHA-256 hash): 2cf24dba5fb0a... (truncated for readability)
This simple process ensures reliable security and data verification in seconds.
Advantages of SHA-256 Over Other Algorithms
While older algorithms like MD5 or SHA-1 are considered weak due to vulnerabilities, SHA-256 remains robust and widely trusted. Its 256-bit structure makes it resistant to brute-force attacks and collisions, giving it a significant advantage in modern cybersecurity practices.
Conclusion
A SHA-256 generator is more than just a hashing tool—it is a foundation of secure digital communication, password protection, and blockchain technology. Its irreversibility, consistency, and strength make it an indispensable tool for developers, IT professionals, and businesses. By incorporating SHA-256 hashing, you can add a powerful layer of protection to sensitive information, ensuring safety in an increasingly digital world.